To create a tunnel between a pfSense OpenVPN Server (Site-to-Site mode) and a UniFi Cloud Gateway OpenVPN Client, you'll need to build the client config as a ovpn file and upload it to the UCG.
This guide only covers the Client config on the UCG.
¶ VPN Client Config
This is the config I've come up with:
client
dev tun
proto udp
cipher AES-256-GCM
resolv-retry infinite
persist-key
persist-tun
remote-cert-tls server
remote vpn.exmaple.com 1194
# This is the CA that was generated/used to create the OpenVPN Server cert
# Export the CA from pfSense and copy its contents here (including 'BEGIN CERTIFICATE' and 'END CERTIFICATE')
<ca>
-----BEGIN CERTIFICATE-----
...
-----END CERTIFICATE-----
</ca>
# If you've setup a TLS Key for tunnel encryption and authentication, paste it here.
<tls-crypt>
-----BEGIN OpenVPN Static key V1-----
...
-----END OpenVPN Static key V1-----
</tls-crypt>
# Place the Client Cert and Cert Key you've generated for your client in pfSense in the two following <cert> and <key> tags
<cert>
-----BEGIN CERTIFICATE-----
...
-----END CERTIFICATE-----
</cert>
<key>
-----BEGIN PRIVATE KEY-----
...
-----END PRIVATE KEY-----
</key>Upload this config to Settings > VPN > VPN Client > Create New > OpenVPN > Configuration File
Once you Apply the new config, the Client should attempt to connect to the Server defined in your config.
One thing I found to be misleading is the Tunnel IP / Subnet shows the IP assigned by the server to the client with a /32 subnet mask. If you SSH into the UCG and run show ip route, there should be a route to the full size subnet configured for the tunnel via the new tunnel.
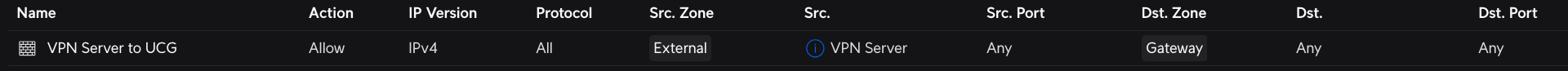
¶ Firewall
By default, all traffic ingressing the UCG via the OpenVPN client tunnel will be dropped as it is part of the External firewall zone.
In my case, I only want to allow the VPN server's tunnel address to be allowed to traverse the firewall and hit the UCG itself (this is for management access to the UCG only).
I created the following firewall rule: