¶ Server
¶ Certificates
1. Create a CA to sign the server and client certs. System → Certificates → Authorities
I created a CA called VPN-PTP-SiteA-CA
2. Create a server cert for the OpenVPN server, sign it with the new CA.
Server Cert: VPN-PTP-SiteA-Server-Cert
3. Create a client (user) cert for each OpenVPN client (remote site).
Client Cert: VPN-PTP-SiteB-Client-Cert
4. Export the new CA and the client cert/key.
¶ OpenVPN Server
1. Create a new OpenVPN server. VPN → OpenVPN → Servers (Add)
2. Configure the server similar to the following:
Mainly, notice the cert config.
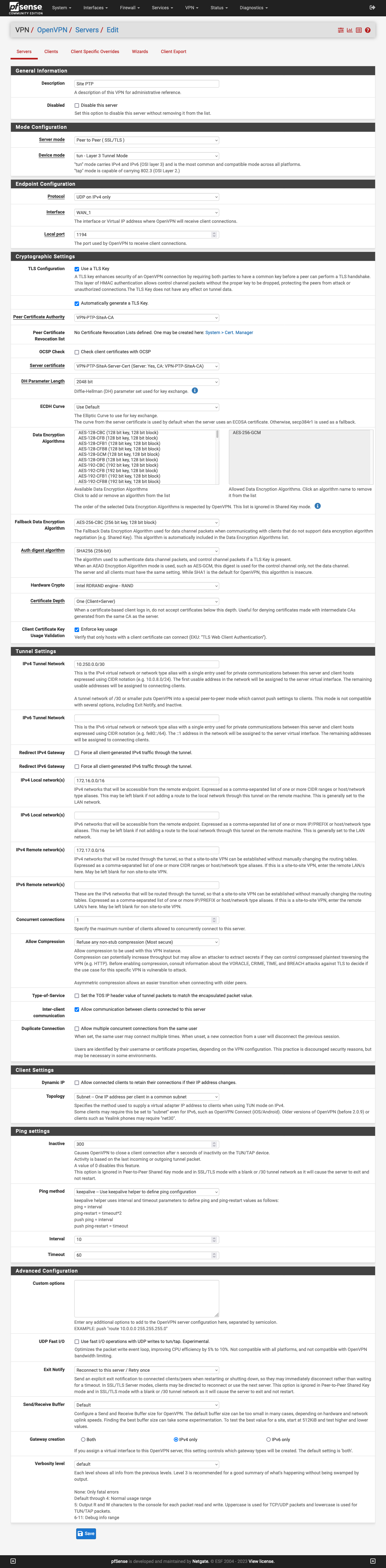
3. Save the config.
4. Open the server config for editing again.
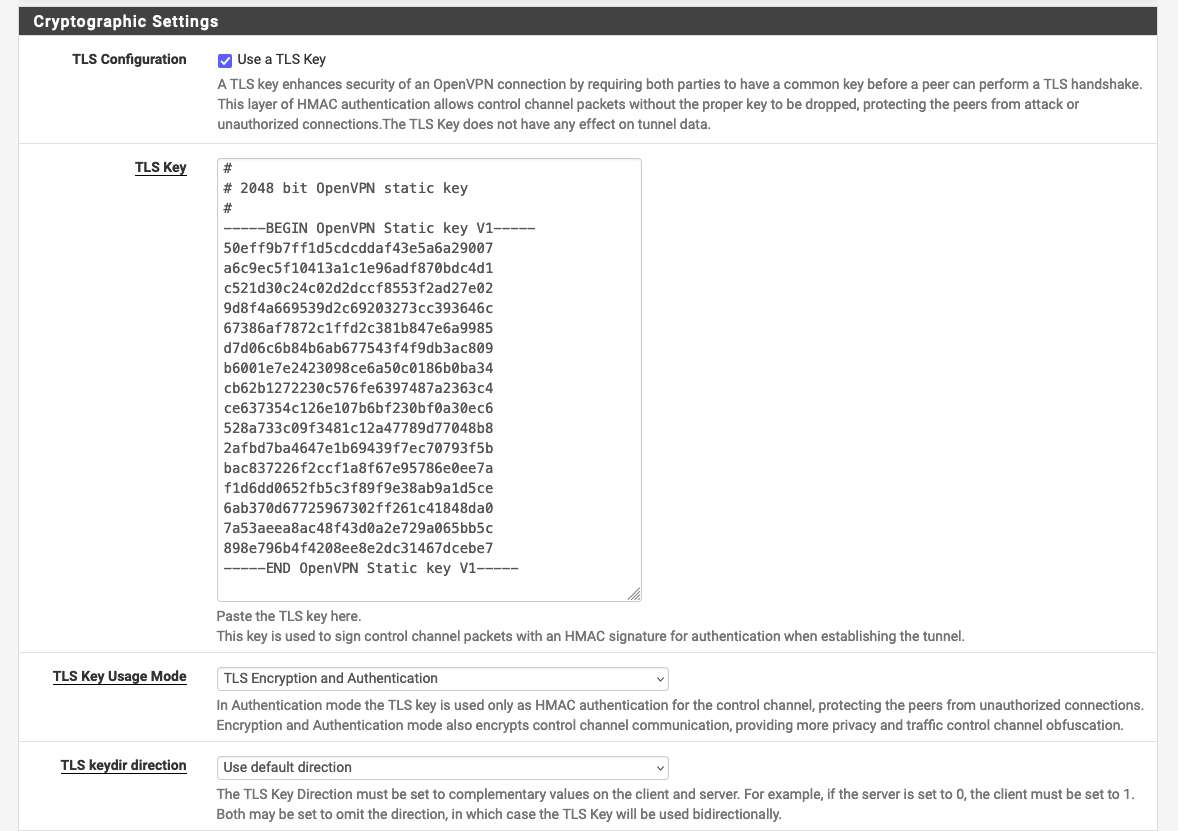
5. In the Cryptographic Settings section, notice the ‘TLS Key', ’TLS Key Usage Mode', and 'TLS keydir direction' fields. Copy the TLS key for use on the client machine. Optionally, set the usage mode to ‘TLS Encryption and Authentication’ (I recommend doing so). Leave keydir as the default.
¶ Firewall
Ensure the proper firewall rules are in place to allow the OpenVPN client to connect via the WAN (public facing) interface
(Internal, site-to-site firewall config covered later)
¶ Client
¶ Certificates
1. Import the CA downloaded from the server earlier. System → Certificates → Authorities
2. Import the client cert/key pair downloaded from the server earlier. System → Certificates → Certificates
¶ OpenVPN Client
1. Create a new OpenVPN client. VPN → OpenVPN → Clients (Add)
2. Configure the client similar to the following:
Uncheck the box to generate a new TLS key, paste in the key from the server. Also make sure to use the CA and client cert that was imported.
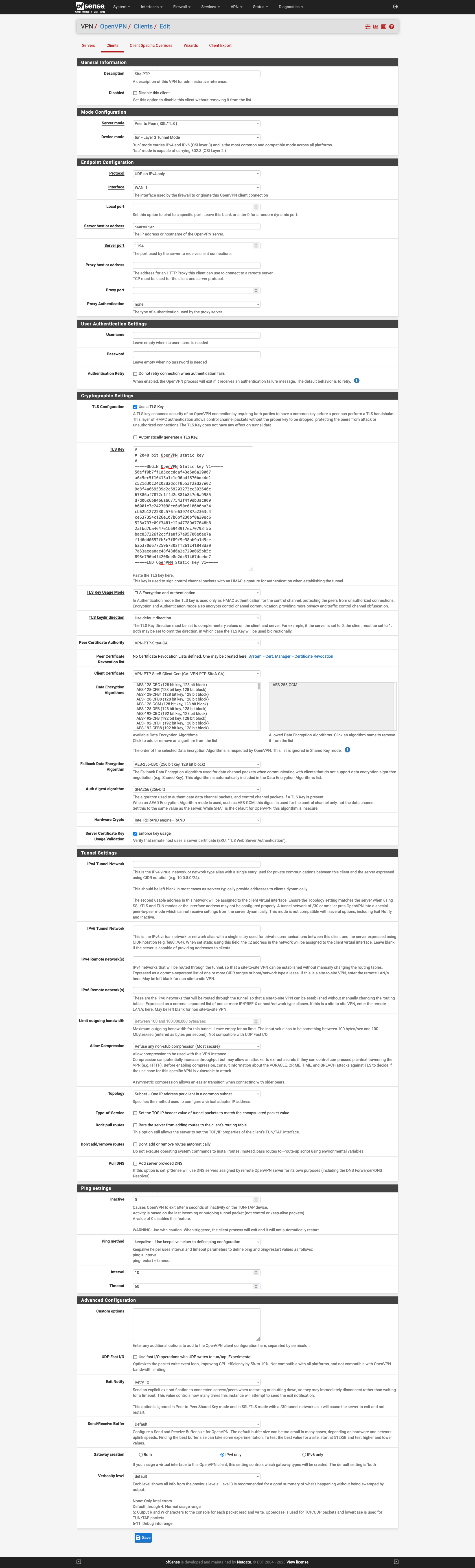
3. Save the client config.
The client should automatically connect to the server.
¶ Site-to-Site Firewalling
1. I like to create the new VPN server/client as their own interface to make firewall config easier.
Add the new server/client under Interfaces → Assignments
2. Edit the new interface, name it accordingly, enable it, save it.
3. Navigate to the interface's firewall tab.
4. Create any desired rules to allow traffic originating from the other end of the tunnel to traverse the new interface. Do the same on the other end.
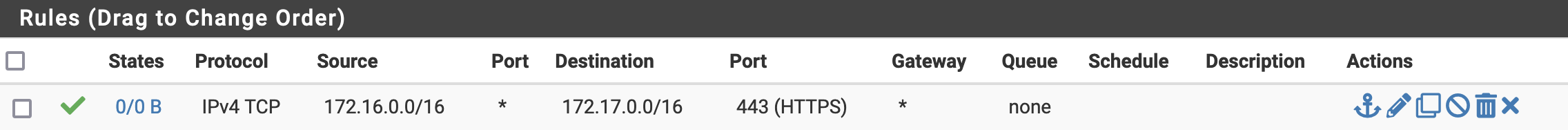
For example, if I wanted to allow HTTPS traffic to flow freely between the two sites (in both directions), I would create the following rules on each respective firewall endpoints.
¶ Site A
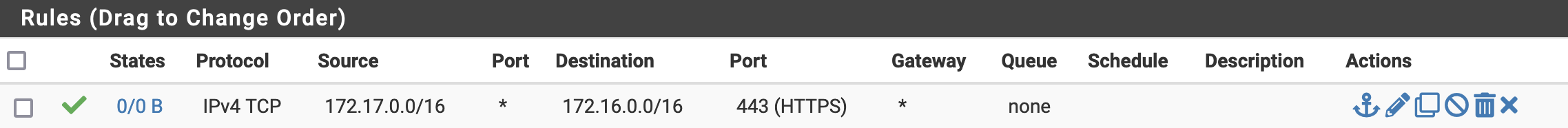
¶ Site B